Mastering in IaaS (Azure Virtual Machine)
It’s been a long I have posted something related to Azure VM . In this post i will tell you all the internal thing about azure virtual machine . CLICK HERE to know how to create a virtual machine with basic Azure Understanding .
Azure VM is a computer instance that you create through Azure portal . it’s almost like Windows Hyper-V VM . You can use Azure portal,CLI,powershell,Visual studio to create a VM . When you create a VM in azure , it create with couple of properties or services . Like Resource Group , Disk , NIC , Public IP .
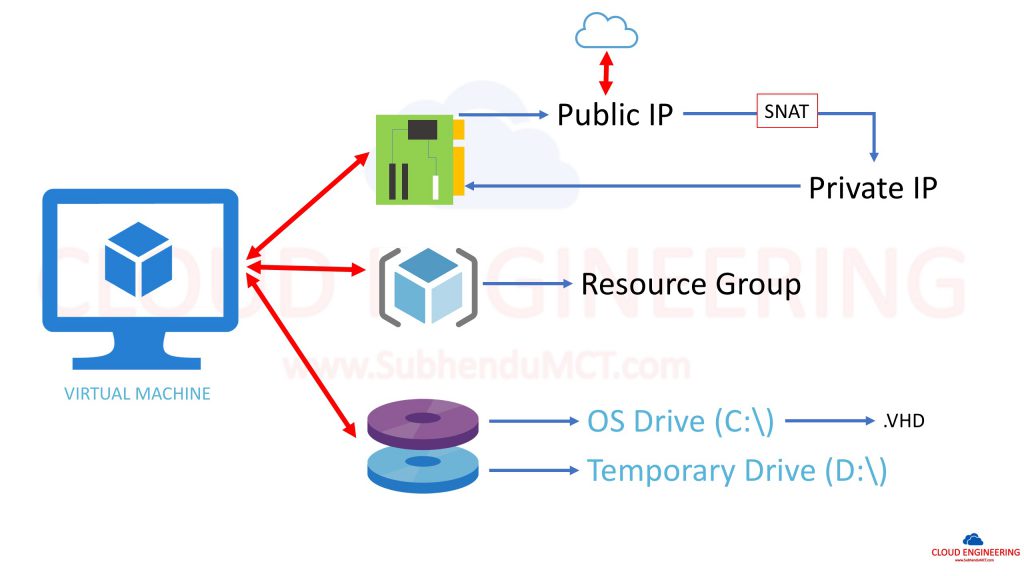
VM Network : Whatever virtual machine we create in Azure that is a Gen-1 vm . During process we define network and NIC card . Azure provide one private IP from that network . If you provide 10.0.0.0/24 network subnet then private IP of that VM will be 10.0.0.4 where first three and last IP are reserved by Azure . Where first IP(10.0.0.1) is reserved for gateway .
A deployment in Azure can communicate with endpoints outside Azure in the public IP address space. When an instance initiates an outbound flow to a destination in the public IP address space, Azure dynamically maps the private IP address to a public IP address. After this mapping is created, return traffic for this outbound originated flow can also reach the private IP address where the flow originated.
Azure uses source network address translation (SNAT) to perform this function. When multiple private IP addresses are masquerading behind a single public IP address, Azure uses port address translation (PAT) to masquerade private IP addresses. Ephemeral ports are used for PAT and are preallocated based on pool size.
VM Disk : During VM creation we also define the disk type for that VM . VM disk could be managed or unmanaged . Managed means managed by Microsoft and unmanaged means managed by you . There are couple of benifit behind chooing managed VM .
When we create a VM in azure it create along with a VHD , where vm all OS files(C;\) and a Temporary drive(D:\) – use for pagefile.sys(Pagefile.sys is the Windows paging file, also known as the swap file, or virtual memory file. It’s a file that Windows uses as Virtual Memory.) . This temporary drive is a part of host hyper-v system where your vm is running . Apart from basis or standard size this temp drive create use SSD in behind . It’s recommended not to keep anything in that drive . During migration of your VM to another host this temp drive will not be migrated .
Resource Group : Resource group is like folder that we normally use in our windows environment . But in Azure it’s more than that . RG is for better manageability and resource grouping based on working culture or support option . It can also be use for RBAC (Role Based Access Control) .
Now let’s have a look of options that we get after VM creation .
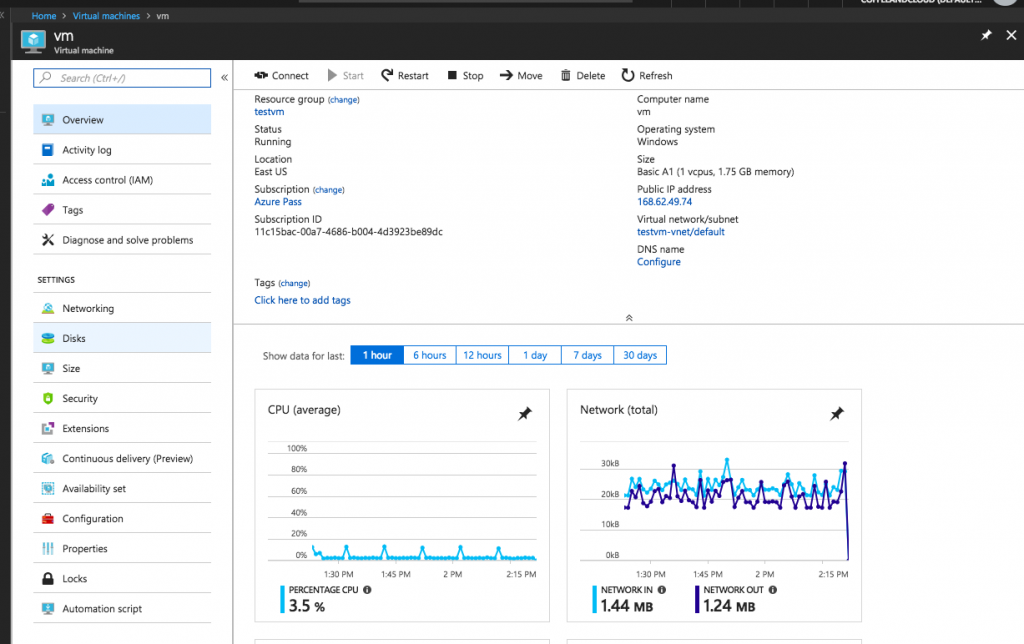
 Overview : In this panel we will get all information about virtual machine like vm name , rg name , public ip , subscription id etc . We will also get some knowldge about CPU , DISK ,NETWORK uses .
Overview : In this panel we will get all information about virtual machine like vm name , rg name , public ip , subscription id etc . We will also get some knowldge about CPU , DISK ,NETWORK uses .
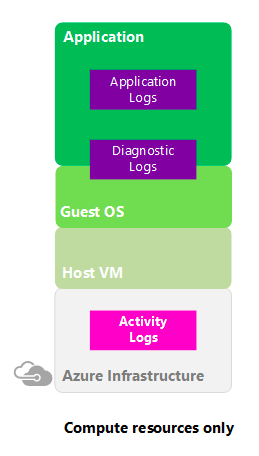
Activity Log : The Azure
Activity Log is a subscription log that provides insight into subscription-level ev
ents that have occurred in Azure. This
![]()
includes a range of data, from Azure Resource Manager operational data to updates on Service Health events. The Activity Log was previously known as
“Audit Logs” or “Operational Logs,” since the Administrative category reports control-plane events for your subscriptions. Using the Activity Log, you can determine the ‘what, who, and when’ for any write operations (PUT, POST, DELETE) taken on the resources in your subscription. You can also understand the status of the operation and other relevant properties. To create alert we can use ALERT section .
The Activity Log differs from Diagnostic Logs. Activity Logs provide data about the operations on a resource from the outside (the “control plane”). Diagnostics Logs are emitted by a resource and provide information about the operation of that resource (the “data plane”).
Access Control (IAM) or Role Based Access Control (RBAC) : Authentication and Authorisation is two main factor in every company . To provide granual control to users to use Azure we need to provide access to users . To provide this kind of access can use RBAC . RBAC is Role Based Access Control . Based on person role we can assign permission . Too many permissions can expose an account to attackers. Too few permissions means that employees can’t get their work done efficiently.
to be continued ..